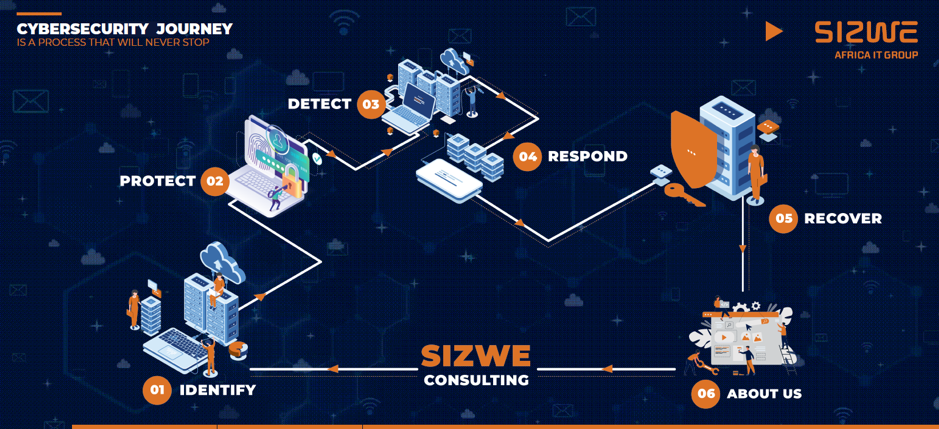
Sizwe Cybersecurity Journey: About Us
Steps of the Sizwe Cybersecurity Journey: Part 4
Today’s article by Sizwe Africa will cover the final step in the Sizwe Cybersecurity Journey, discussing more about the company and its processes.
Step 6: About Us
It is always recommended to scan through everything to ensure that potential risks can be avoided and to secure your data.
Step 6 is to contain malware that could already be within your network. You will then need to scan for vulnerabilities to accurately establish your current level of risk, and then workshop the results to be able to create a security improvement plan.
Cyber Risk Assessment
Contain malware that may already be inside your network, scan for vulnerabilities to establish your current level of risk, and then Workshop the results to create a security improvement plan.
vCISO
Rather than pay a full CISO salary, use our Virtual CISO offering and use the culmination of our security practitioners years of cybersecurity and industry experience to help you develop and manage the implementation of your organisation’s information security program. The money saved can be spent on a layer of defence you may not yet have and need.
Solution Design, Implementation, and Support
Our solution architects and service delivery teams provide customers with knowledge and vision to successfully plan, design, and implement their technology investments using proven methodologies drawn from experience.
Cybersecurity Architecture Design
Our team of cyber security experts can assist with the develop and design of a cybersecurity architecture across IT systems, networks and applications
Our service includes:
1. Identifying risks that arise from existing and future solution architecture design.
2. Selecting the appropriate security products and technologies to meet a security requirement.
3. Incorporating best practice and the latest architectural frameworks.
4. Ensuring adherence to important security architectural characteristics.
5. Designing and creating standardised procedures for preserving a system or solution’s security throughout the course of its entire lifespan.
For more cybersecurity related content visit the Sizwe Africa IT Group Newsroom.
By Aadiel Ayob, Executive – Innovative Enterprise Services and Solutions at Sizwe Africa IT Group
