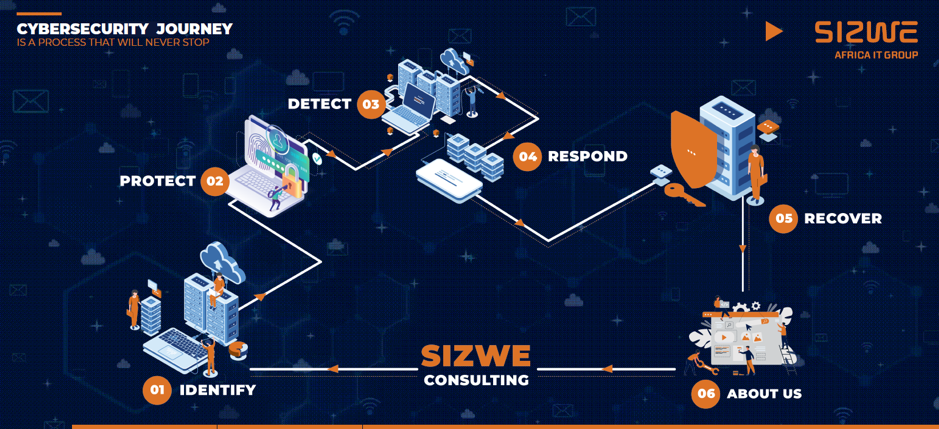
Sizwe Cybersecurity Journey: Identify and Protect
Steps of the Sizwe Cybersecurity Journey
October is cybersecurity month. To help you and your company stay ahead of cyber threats, the team at Sizwe Africa are sharing the steps to their very own cybersecurity strategy in a series of articles. In today’s article we’ll cover the first two steps: Identifying vulnerabilities and protecting against cyber attacks.
Step 1: Identify
Step 1 involves identifying the problem through zero trust. We can no longer assume that internal entities are trustworthy. We need to directly manage the security risk by frequently checking for unusual access attempts.
The following items are covered when identifying cybersecurity threats:
Zero Trust
A strategic security strategy called “Zero Trust” is based on the idea of removing trust from a company’s network architecture. Trust is neither absolute nor enduring. We can no longer take for granted that internal entities are reliable, that they can be directly controlled to lower security risk, or that one check is sufficient. Every time you seek to get access, the zero-trust model of security forces you to reconsider your assumptions of trust.
Software Defined Access
In your office, Software Defined Access (SD-Access) offers zero-trust security. It protects access to your apps and software defined network environment for all users, all devices, and from all places.
Privileged Access Management
Access to privileged accounts is restricted by Privileged Access Management (PAM), which also tracks when accounts utilise any elevated rights. Privileged accounts, as used in this illustration, are any user or administrator accounts with certain heightened privileges.
Penetration Testing
Penetration testing is an effort to access corporate assets or data without the target being aware. We may concentrate on your WiFi network, external network, web applications, firewalls, mobile applications, or internal or internal networks with WiFi. The ideal place to start would be with a Vulnerability Assessment, however we can customise the penetration test to your needs. Close all the apparent entrances first before asking us to attempt to enter.
Vulnerability Assessment
What users do with data is frequently more crucial than the data itself when undertaking vulnerability risk management. Today, the bulk of OS types and systems have the majority of serious vulnerabilities that can be found by all vulnerability scanners. A greater difficulty is converting that data into useful insight when a scan returns hundreds of vulnerabilities. We can assist you in determining which vulnerabilities should be fixed first in order to significantly lower your risk with the smallest amount of work.
Cybersecurity Asset Management
Cybersecurity Asset Management is the process of identifying the IT assets that your company has and the possible security flaws that may impact each one on an ongoing, real-time basis. Assets come in numerous forms. They may be specialist IoT, IoMT, IloT, or OT equipment or regular devices like PCs and servers.
Step 2: Protect
Step 2 involves ensuring that threats are stopped immediately before they reach your network or endpoints. We can do this by analysing and learning internet activity patterns. Step 2 includes:
DNS
Umbrella blocks attacks at the DNS layer, preventing them from ever reaching your network or endpoints. Umbrella automatically detects attacker staging for existing and new threats by analysing and learning from patterns of internet behaviour. It then proactively prevents requests to dangerous sites before the connection is made or a malicious file is downloaded. Additionally, Umbrella may prevent infected computers from leaking data via callbacks to an attacker’s botnet infrastructure (C2).
NGFW
A network security device called a next-generation firewall (NGFW) has features that go beyond those of a conventional, stateful firewall. A next-generation firewall contains additional capabilities like app awareness and control, unified intrusion detection and prevention, and cloud-delivered threat information, while a classic firewall normally offers stateful inspection of both incoming and outgoing network traffic.
SD-WAN
The utilisation of IP security (IPsec), VPN tunnels, next-generation firewalls (NGFWs), and micro segmentation of application traffic are the main components of SD-WAN security.
ZTNA
In order to safeguard all access across your apps and environment from any user, device, or location, Zero Trust delivers a complete solution. You may reduce dangers in your environment by detecting them early on and taking appropriate action.
Network Detection and Response
In order to identify suspect network activity, network detection and response (NDR) systems combine sophisticated analytical methods that are not signature-based, such as machine learning. Teams may now react to risks and abnormal or malicious communications that other security technologies might have missed.
Endpoint Security/EDR
A fully integrated endpoint security solution, endpoint detection and response (EDR), or endpoint threat detection and response, combines real-time constant monitoring and gathering of endpoint data with rules-based automated reaction and analysis.
To defend against junk mail, malware, and other risks that are largely delivered over email, a strong email security system is essential.
Patch
The goal of a patch management policy is to manage and mitigate risks in your organisation via a consistent, well-documented patching process.
SASE
In order to provide safe access to applications wherever users are working, Secure Access Service Edge (SASE) integrates networking and security capabilities in the cloud. SD-WAN, firewall as a service, Secure Web Gateways (SWGs), Cloud Access Security Broker (CASB), and zero Trust Network Access are among the primary features (ZTNA). The SASE model aims to merge these functions—which were previously provided in a variety of discrete point solutions—into a singular, integrated cloud service.
DLP
No matter where critical data is located in your clouds, find it and safeguard it. Ensuring compliance while preventing data loss, exfiltration, and unintentional public disclosure. Use sophisticated data loss prevention to enable secure productivity on the web, in the cloud, and with email.
CASB
Regardless of whether a cloud application is managed or unmanaged, you can easily identify and control its usage with the help one, integrated cloud service (CASB) solution. This stops risky employees or malevolent hackers who have infiltrated your perimeter from stealing sensitive data from your environment.
WAF
While conventional firewalls aid in defending private networks from harmful online apps, WAFS aid in defending web applications against dangerous users. By screening and monitoring HTTP traffic between a web app and the Internet, a WAF aids in the protection of web applications. It generally guards against attacks like cross-site scripting (XSS), file inclusion, SQL injection, and cross-site forgery, among others.
FWaaS
The more recent paradigm for providing firewall capabilities over the cloud is firewall-as-a-service (FWaaS). Another name for this service is “cloud firewall.” Similar to how conventional firewalls enclose an organisation’s internal network, FWaaS creates a virtual wall surrounding cloud platforms, infrastructures, and applications. FWaaS is often more effective than conventional firewalls in securing cloud and multi-cloud assets.
MFA
Utilise an MFA solution to proactively lower the chance of a data breach. Verify users’ identities, obtain insight into every device, and implement adaptive rules to control access to each and every app.
ZTNA
Any access to your apps and environments, from any person, device, or location, may be secured with the ZTNA solution. ZTNA is a strategic security strategy that is based on the idea of removing trust from a company’s network architecture. ZTNA models continually verify trust before allowing just the necessary access and treat all resources as external.
NG SWC
A new cloud-native solution called a Next Generation Secure Web Gateway (SWC) may shield businesses from the rising number of sophisticated cloud-enabled attacks and data concerns. The conventional secure web gateway, commonly referred to as a web proxy or web filter, has logically evolved into this. A Next Gen SWG deals with both online and cloud traffic, unlike a standard secure web gateway, which only handles web traffic and is unaware of cloud-enabled threats and data hazards for individual instances of managed applications, thousands of shadow IT apps, and cloud services.
Want to learn more about cybersecurity this cybersecurity month? Head on over to the Sizwe Africa IT Group Newsroom for the latest cyber security news and tips.
By Aadiel Ayob, Executive – Innovative Enterprise Services and Solutions at Sizwe Africa IT Group
